Security
How to bypass ChatGPT blocks
Are you being blocked from using ChatGPT by your school, university or workplace. Look no further. By simply signing up for VanishedVPN, we will take all of that pain away. Our innovative solution means that you are free from those pesky blocks on whatever device you choose.
- Sign up for a subscription here
- Connect to our Aus , UK or USA VPNs
- Enjoy block free ChatGPT and all other AI Apps.
#AI #UnblockchatGPT #ML

How to stop Google from spying on you
Remember when you clicked ‘accept’ on the terms & conditions when installing or signing up to a Google service without reading the 100+ pages ?You were actually giving Google permission to create a profile about you with everything that they know, and keep that data to use for their own advertising , or to sell on. Have I got your attention ? Then read on…
The smartphone that you carry with you everywhere stores a lot of data about us. Our phones know what we do, where we are, and what we want. Every hour of every day.
And it doesn’t end there. Our ISPs, browsers, search engines, the apps we’ve installed, social media platforms, governments, Google, and other websites we visit all know what we’re doing online.
So let me ask you a question: do you have something to hide?
Of course you do. Everyone does.
This might be news to you, but your data (juicy or not) is worth big bucks and there are a lot of people who want it.
Why do companies want my data?
Because big data is big money.
Governments want to know what you are doing. Marketers want to know how you spend money. And there are bad folks out there who just want to take it. It’s a privacy nightmare.
Google, Facebook, Amazon, Apple, and Microsoft store so much user data that it is believed that it will be collectively worth $6 trillion by the end of 2020.
How do companies make money from my data?
Google, Facebook, Apple etc. make money by knowing you really well. They want to build a profile of you which can be used to target adverts. The more they know about you (your age, sex, family, what you like, what you don’t like, your finances), the more money they can sell you for. Kind of like pimps. Kind of like data pimps.
So why do people put their trust and their personal information into the hands of these companies, you ask?
They don’t. Well, not knowingly at least!
Most people don’t realise how much data Google and other companies really gather.
Do you? Let’s do a quick privacy check together.
What does Google know about you?
- Google stores search history across all your devices on a separate database, so even if you delete your search history and phone history, Google still stores everything until you manually delete everything, and you have to do this on all your devices.
Check yours: https://myactivity.google.com/myactivity
- Google stores your location every time you turn on your phone, and you can see a timeline from the first day you started using Google on your phone. It records every place you visit, the time you get there and how long it takes to get to that location from your previous one.
Check yours: https://google.com/maps/timeline
- Google creates an advertisement profile based on your information, including your location, gender, age, hobbies, career, interests, relationship status, possible weight, and income.
Check yours: http://google.com/settings/ads/

- Google stores information on every app and extension you use, how often you use them, where you use them, and who you use them to interact with (who you talk to, what nationalities your friends are, what time you go to sleep)
Check yours: https://security.google.com/settings/security/permissions
- Google stores all of your YouTube histories. Based on your Youtube search and watched videos, they can determine if you’re a conservative, progressive, Jewish, Christian, or Muslim, travelling, or a stay at home mum. They know it all.
Check yours: https://youtube.com/feed/history/
Download your Google data
You can download your own archive of everything you have stored in Google’s services. Here’s how:
- Go to http://takeout.google.com/settings/takeout
- Select the products that you want to back up. I decided to select everything.
- Click ‘Next’ at the bottom of the page.
- Choose the file format – you can pick a .ZIP file and choose a maximum size. I recommend going with the full 50GB file to avoid having your data split into multiple files. If you choose 2GB and have a lot of information on Google, for example, you’re going to have a lot of ZIP files. Choose 2GB if you’re on an older computer, since ZIP files larger than 2GB require newer operating systems.
- Choose your delivery method. You can get a link via email or have the archive sent to Dropbox, Google Drive or Microsoft OneDrive.
- Tap “Create Archive.”
- Be patient. Google warns the archive may take hours or days to create.
Remember, downloading the data doesn’t delete it from Googles servers. Think of it as a backup.
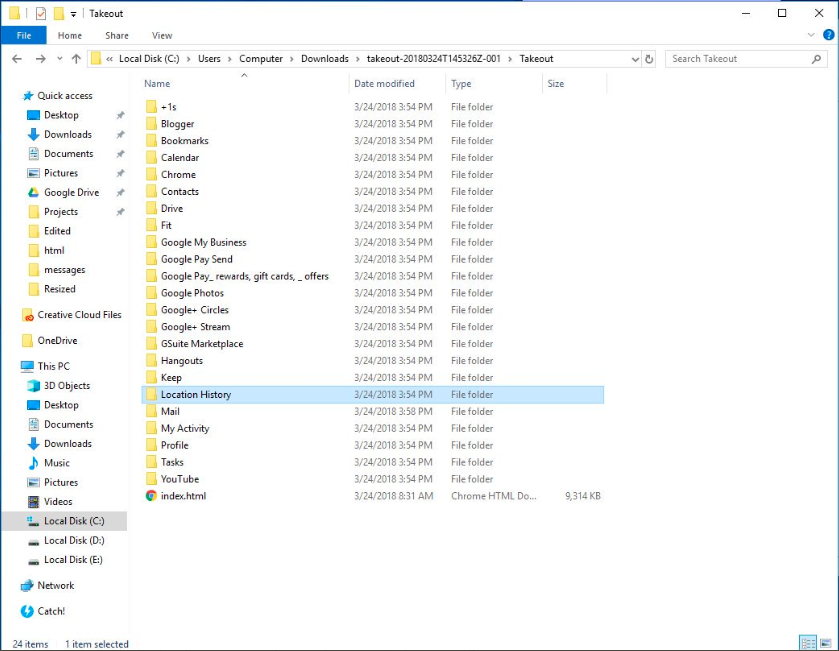
Its quite frightening that Google knows every entry in my calendar. It shows all the events I have ever added, whether I attended them, what time I attended them and when I left the venue.
Google activity file shows every Ad I ever viewed or clicked , every website I visited and what time I did it, and every app I’ve installed. Every image I’ve ever searched for is there, and every new article and google search I’ve ever made.
Google is not your friend. You can’t trust them with your data. They sell whatever data they can get their hands on — to the highest bidder, and then the lowest bidder, and every bidder in-between.
Is it only Google I should be worried about?
Absolutely not…
Facebook, and Amazon are amongst the other big players who are up to no good too. And Siri & Alexa are also in on it. Ever wondered why just after you’ve been talking about something, an advert related to that discussion pops up in your ad feed ? We’ll be publishing another blog on all of this..
Why should you care about private browsing?
So far we’ve learnt that data dominates the digital world. Therefore, any time you visit a website, you leave a trail of data behind you. And everybody wants it, from cybercriminals to enterprise giants. Every day, millions of trackers are hunting, and your data is the big prize.
We can’t stop it altogether but there are plenty of things that we can do to reduce our digital footprint.
Now, let’s talk solutions.
Use a VPN
Using a Virtual Private Network (VPN) is the best way to protect your privacy when you’re browsing the web. A VPN sends your Internet traffic through an encrypted tunnel, making it extremely difficult to intercept, track, or read your data.
As soon as you connect to the VPN, everything you do online is anonymous.
You’re invisible.
Any websites you visit.
All files you download.
They all become out of sight from any and everyone.
Now, a VPN won’t stop Google from targeting you with tailor-made ads. But it can hide your identity.
Vanished VPN is one of the best value VPNs in the world, and has been recommended by Lifehacker.
When you use VanishedVPN Google will see one of our IP addresses – and your real IP address given to you by your ISP will be hidden from sight. Google, Facebook, or anyone tracking or monitoring your online activities, will not be able to identify you as the user.
What’s your online privacy worth?
Browse in Incognito
Browsing in private mode (or incognito) gives you a few privacy enhancements, and is the simplest thing you can do to make some of your general internet usage a bit more anonymous. Better than nothing. Technically.
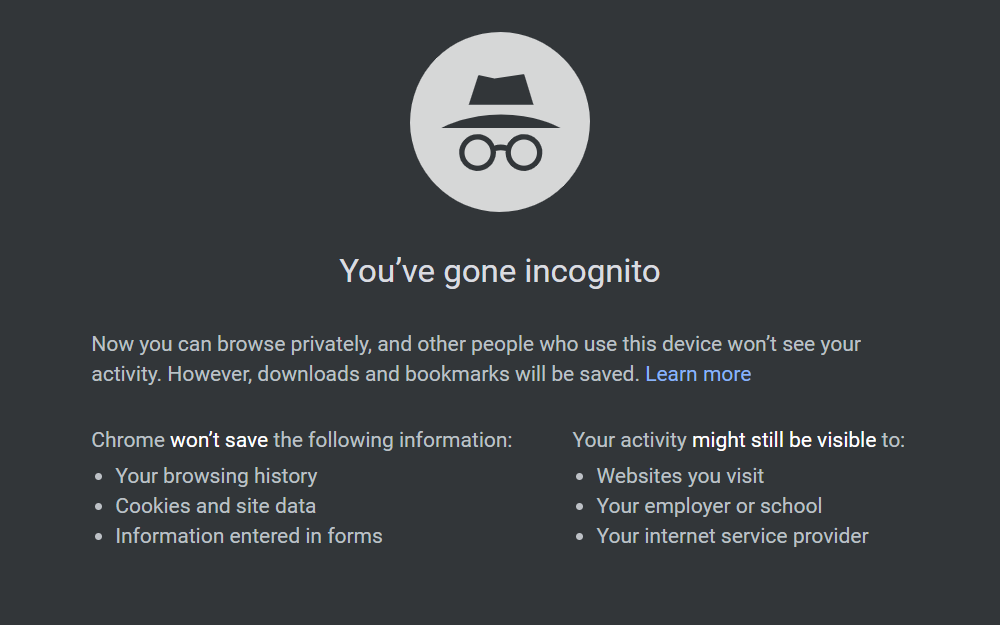
When you launch incognito mode, your browser doesn’t store your history, searches, and cookies for later. Once you close your private browser window, anyone who uses your device after you won’t be able to see what you did. However, your internet provider, your employer, your school, your government, or the sites you visit can still see and record your browsing data.
Solution: We recommend you use a service like DuckDuckGo. This an independent search engine that strives to keep your search history private and block advertising trackers which in turn give you control of your data.
Don’t use Chrome
Chrome is the most widely used web browser in the world, but remember, it is a google product, and designed to harvest data for Google. There are other browsers available which don’t have such close alligiences to Google
Clear your Flash cookies
Flash cookies (also known as Local Shared Objects) aren’t like normal cookies, although they function similarly. They save your settings, preferences and browsing data when you go to websites that use Adobe Flash. And yes, they’re exactly as boring as this paragraph was.
Removing Flash cookies ensures you’re not leaving any crumbs of personal activity behind after you flush out all the other regular, easy-to-delete browser cookies. To get rid of them, go to the Adobe Settings Manager in your browser, and clear some or all of your Flash cookies through the storage panel.
Important as it is, clearing your Flash cookies doesn’t encrypt and secure your browsing, searches, online banking, etc. It’s just a routine chore you should once in a while, like taking the bins out. You’ll technically make things cleaner but you shouldn’t go patting yourself on the back.
How to delete the data Google stores
After reviewing the data that big G has on you, you can delete all or some of it by following the instructions here.
Wrapping up
Signed into Google? Then you’re being tracked across searches, emails, locations, and more. That Microsoft Account you use to log in to Skype, Outlook, Xbox Live? Also being tracked. Your Apple ID? They’re not thinking differently about your data. I could go on and on and on…
You get the point. Whether you sign up for online services, or you don’t sign up for online services — you’re constantly getting tracked.
Everyone wants your data, and they will do anything they can to take it.
If you are serious about your privacy, then always use a VPN, and take the additional measure described above.

Using public wifi without a VPN ? Be prepared to be hacked.
Free public WiFi seems like the best thing since sliced bread.
Free, easy to use, decent speed, unlimited browsing.
What’s not to love?
A lot, actually. So let’s get started.
Free public WiFi hotspots can be a trap. They are open, unsecured and relatively easy to hack. They open up a whole new world of possibilities for hackers to invade your privacy, collect your personal and financial data, or even break into your device.
There are over 100 Million public wifi hotspots available to us, but a staggering 89% of these are not secure.
So what ?
All the traffic within a public WiFi network is usually unsecured, meaning it does not use proper encryption to protect your internet data. Your sensitive information sent via an unsecured WiFi network (such as credit card numbers, passwords, chat messages) becomes an easy target for hackers.
When it comes to stealing your data, hackers get quite creative. One of the ways they attack is called man-in-the-middle (MITM). Cybercriminals will create their fake public network. In most cases, the name will be similar to the name of the place with access to a public network (like a restaurant or hotel) nearby. Then, hackers will snoop on your private information and target data on your devices.
On top of that, hackers can install packet sniffing software. It is particularly dangerous because it records massive amounts of data which later can be processed on their demand.
Childs play
A recent ‘ethical hacking’ demonstration, a 7 year girl took 10 minutes 58 seconds to set up a rogue network on public wifi, and begin to intercept personal data from users on the same network.

How do hackers exploit public wifi
Here are just a few of the ways that you can be hacked.
Evil Twin attack
In an Evil Twin attack, cybercriminals create a fake network with a name that is very similar to the actual legitimate wifi name. For example, if a coffee shop provides a wireless guest network named “CoffeeShop_Guest,” hackers will create a similar network of their own and call it “CoffeeShop_FREE.” Once connected to the evil twin, all your network traffic becomes visible to the hacker behind it.
Man-in-the-middle attack
In MITM attacks, hackers spy on your browsing activity, waiting for the perfect time to strike. To put it simply, the cybercriminal stands between your device and a website or service you are trying to access. From there, the hackers have the ability to intercept and alter all your communications and access sensitive information like banking credentials, passwords, cryptocurrency wallets, and even your private messages from auntie Doris begging you to stop sending her invites to play Candy Crush.
Malware injection
A malware attack is especially nasty and can occur when cybercriminals inject malware into unprotected WiFi hotspots and compromise your internet traffic. These attacks are extremely difficult to detect and a real pain to get rid of. On an unsecured WiFi network, malicious code can slip into your device at any time – when shopping for a new wine rack, or just browsing the Gram while sipping your morning avocado iced coffee.
Cookie side-jacking
Cookie side-jacking is one of the oldest forms of cyber-attack. When you are connected to an unsecured public WiFi, hackers can get their hands on your cookies. The same cookies that store your login details on your computer so you don’t have to enter your username and password every time you open a website. And stealing this information is easier than you think.
Nasty worms
While most people are usually familiar with viruses, not many people have heard of worms. The difference between the two is that the viruses require you to download a file, while worms can infiltrate your device, even if you don’t visit any shady sites. If a Wi-Fi network lacks proper security, worms can easily find their way to you and can compromise your data.
WiFi sniffing
With the help of pretty basic software, which is simple enough to use and legal to get, hackers can spy on your online activities, see your login information, steal your passwords and break into your online accounts if you’re browsing on an unsecured network. Somehow even creepier than sniffing stranger’s hair in public, and that’s a pretty low bar to set.
In 2017 Belgian researchers discovered that WPA2 protocol used by the vast majority of WiFi networks is unsafe.
According to the report, the WPA2 protocol can be broken using novel attacks potentially exposing personal data.
The vulnerability can affect a broad range of operating systems and devices – including Android, Apple, Windows, Linux, OpenBSD, MediaTek, etc. Basically, if you have a device that connects to WiFi, it can be affected. The situation is a little different in the European Union since the General Data Protection Regulation (GDPR) took effect. ISPs processing Europeans’ data must be compliant to the GDPR. They have to make sure they store personal data only with the consent and when it’s not linkable to an individual.
So how do I stay safe on public wifi
Using a VPN is the only way to be certain that you cannot be hacked while using public wifi. Think of it as a condom for your data.
Vanished VPN is one of the best value VPNs in the world, and we consistently out perform our competitors in terms of speed. We have apps for your devices, and easy setup guides.
Check out our great value plans today , and wave goodbye to hacking worries.

You’re Not Using a VPN for your Business? Bad Idea.
Barely a week goes by without news of a major cyber incident being reported, and the stakes have never been higher. Data theft has become commonplace; the scale of ransom demands has risen steadily; and cumulatively the environment in which businesses must operate is increasingly hostile. The cyber threat has become the unavoidable cost of doing business today.
Ransomware, spear phishing, malware, drive‑by attacks, DDoS attacks – the list goes on and on. While cyber attacks that make the news are often large in scale, make no mistake that small businesses are being attacked, too.
In fact, small businesses may be more vulnerable to cyber threats than large corporations.
Let’s take a look at some cyber security facts, presented to us by Hiscox’s that will blow your mind!
The number of firms reporting cyber incidents has risen from 45% in 2018 to 61% in 2019.
The mean figure for losses associated with all cyber incidents among firms reporting attacks has risen from $229,000 last year to $369,000 – an increase of 61%
The mean cost of cyber incidents has jumped from $34,000 a year ago to a fraction under $200,000. For large firms, there has been an 18-fold rise to $395,000. The comparable figure for small firms is $9,000, up from $3,000 in 2018.
Given those stats, cybersecurity should be of utmost concern if you’re going to put your business or services online.
When it comes to the precautions small businesses can take in terms of IT security, many of them are obvious. These include ensuring that antivirus software is up to date and ensuring that company networks are behind well-configured firewalls.
But there’s always more you can do, and one thing well worth considering is the use of Virtual Private Network (VPN) solutions. A VPN; with its highly encrypted tunnel that exits at a remote location is a great defence from cyber attacks, with protection for company assets, which is stronger than a traditional firewall, and therefore more secure from a data breach.
What extra protection can VanishedVPN offer my business?
We’re glad you asked. Let’s go over some key features together.
• Digital security for your entire team
We secure your business data from cybercriminals by using military-grade encryption.
• Safety on any Wi-Fi network
We encrypt all your online activity, including the files you share or the emails you send.
• Dedicated global IP address
Connect to the country VPN of your choice, and you will be allocated an anonymous IP address that cannot be traced back to your business, protecting you from cyber criminals.
• Protection for your company data in the office and on the go
Connect to VanishedVPN servers at any time, for as many times as you want.
• Unrestricted global access
Bypass geo-restrictions & access blocked content and services from anywhere in the world.
All in all, from small companies to huge corporations, nobody is immune to digital threats. That’s why VanishedVPN is perfect for organisations of any size.
You don’t need to be a technical genius to use our service either! VanishedVPN provides a dedicated infrastructure that’s easy to use for you and your colleagues. It effortlessly integrates with your company’s existing platforms and protects every one of your devices — computers, laptops, phones and tablets.
With VanishedVPN, your entire team can securely access company resources remotely, connect to any public Wi-Fi, and explore geo-restricted content.
So… why aren’t more businesses using a VPN?
They are! And sixty percent of those that are not, said that lack of budget is the main challenge.
That’s why here at VanishedVPN, we offer affordable prices so even small businesses can take steps to counter the ever‑evolving threat of cyber attacks and become cyber ready.
Don’t get caught in the landslide of cybercrime and join the majority of small businesses that are protected online today. We’d love to help you!
Contact sales@vanishedvpn.com to discuss your requirements, or WhatsApp +61 466 383 501

The essential apps for Digital Nomads
Being a digital nomad is a much desired goal for many people. Travel the world and work as you go. If you get the formula right, the world is your oyster with unlimited potential. Working from exotic locations around the globe, moving from place to place whenever you desire. I’ve been working this lifestyle for so long now that I can’t think of any other way to work. If you are looking to live and work like this, there are thousands of blogs and websites that show you how to become a digital nomad, and so many more that list the essential apps you need to make this lifestyle a success. This is our list of the essential apps for digital nomads that you should be using and how to be secure.

1: VanishedVPN – get a plan now
One thing that so many of these digital nomad websites and blogs seem to miss out on is security. If you want to take this lifestyle seriously and make it a success, security should be your number one priority. It seems so easy to connect to free wifi networks at places like Starbucks, McDonalds or the zillion other cafes, bars and hotspots you can now find world wide. But, how many of these have generated a message on your device of “unsecured network” when you try to connect. This should send chills down your spine, as it means you are open to abuse. A simple man-in-the-middle attack, for example, can be so easy to execute on these networks, and you should protect yourself. This is where VanishedVPNcomes in. A VPN provides a secure, encrypted connection from your laptop, mobile phone or tablet to one of our servers around the world. With a VanishedVPN connection all browsing, and communications from your device are secure, and private. If you want to be a digital nomad, you should not be without this.
Plus, the added benefit of using VanishedVPN is that wherever you are in the world, you can connect to our country specific VPN servers to unblock geolocation content and watch TV, Netflix USA, BBC iPlayer and sports (UFC, Formula 1, Premier League etc).

2: Cloud storage
Which ever service you use (Dropbox, Google Drive, iCloud, SugarSync etc) cloud storage is going to be absolutely essential to your chosen lifestyle. Not only does it provide access to all your files from any device, it keeps your valuable documents safe and sound, and easily accessible in case of a lost or broken device. No longer will you have to carry around external hard drives, or even have to worry about a hard drive failure. The only drawback is you need an Internet connection to access your online-only files.

3: Trello
In terms of organising your shit, Trello is the one to turn to. With Trello you can create numerous boards for each project you have, and organise them however you like. The flexibility allows you to keep track of any personal or business task or project from simple to-do lists to project management tasks. You can collaborate by inviting other users to access a board that you set up. This makes working with clients so much easier as they can drop in, add their thoughts & requirements to a board you have created and easily drag-and-drop cards between lists to keep track of things and even prioritise items. Whats more, it’s free.

4: Google Docs
You are going to need a set of apps to write documents, build spreadsheets and create presentations. Google Docs is the perfect way to do this, with all your documents stored online in your own Google Drive, and what’s more, you can export to multiple different formats such as PDF or Microsoft Office compatible documents. One big advantage is you can share documents so you can collaborate with other people.

5: WhatsAPP
From travelling the world, to so many different countries, I have found WhatsApp to be most invaluable. From keeping in touch with friends and family, to setting up group chats with clients, WhatsAPP is the essential communication tool for any digital nomad. Plus, with the added feature of video and/or audio calling over wifi, if you have an internet connection you can have face-to-face meetings with your clients to build confidence. Plus, all communication is encrypted so it’s secure.

6: Gmail
One of the best email accounts you can have. There are many others out there to use, but Gmail is rock solid, easy to use and comes with cloud storage and access to Google Docs, and it’s free. You can use you own email client, Outlook, MacMail, the Gmail app on your laptop, mobile phone or tablet. When all else fails, just log in to http://gmail.google.com.

7: Contacts, Calendar and reminders
You will need cloud based contacts, calendar and reminders apps. Which ever one you chose this will be your life saving app in terms of keeping track of what you need to do, and when you need to do it. Whether you use a native system (such as Apple iCal and reminders) or use the suite of apps provided by your Google account. Just make sure you can synchronise this data across all of your devices, so no matter where you are or what you are doing, you know where you should be and what you should be doing.

8: Password Management App
We are not going to recommend a specific app for this for the simple reason that they all come with pros and cons. Security should be one of your highest priorities, regardless of whether you are a digital nomad or not. Password management is problematic at best. Use a suitably secure password made up of uppercase, lowercase characters with numerics and special characters, and use a different one for each and every service you log into. I have at least 40 passwords I need to remember, and with each one be different, the more I add, the more complex it becomes. A password management app can solve this problem by using unique, complex passwords for each of your logins. All of this is securely encrypted and stored, and locked behind a single password. Great. The con is, lose that one password and that’s it. You are locked out of everything.

9: A decent mirrorless camera
If you are travelling around the world you will want a better camera than the one in your phone. You must invest in something that will be light-weight, compact but versatile. The moment you start taking travel photos you are going to realise you need a camera with multiple lenses, and your phone camera is not really going to cut it. The top four brands to chose from are Canon, Nikon, Sony and Fuji. With a decent body and at least two lenses you are going to want to spend around £2k for a kit. But trust me, it will be worth it. Along with your decent camera you are going to want a subscription to Adobe Photoshop and Lightroom plan to manage and edit your pictures like a pro. Trust me on this one, you want these on your laptop, you need these on your laptop.

10: Noise cancelling headphones.
Whether you do or in ear, or over ear, noise cancelling headphones are going to save your life. There are many brands out there, but we recommend either Bose, Sony or Bang & Olufsen. If you get a pair that will connect to your voice assistant and let you make phone calls even better.

Don’t be the next victim of ‘The Great Hack’ – 9 Ways to secure your data.
‘The Great Hack‘ is a documentary film by Netflix, which details how Cambridge Analytica used our personal data from sources such as Facebook to create profiles of voters who could be targeted to influence events such as the US Elections and the UK Brexit vote. The reality is that we have become far too free with what we share on the internet, and our personal data has now become a commodity which is more valuable than oil.
In this article, we will give you some tips on how you can take steps to secure your personal data.
- We give a lot of our data to companies like Facebook, Google, and Microsoft. But we don’t always know how well that data is protected.
- Data breaches like Collection #1 or attacks like the T-Mobile hack happen way too frequently.
- And companies like Facebook have been criticized for uploading user data without permission.
- You can’t stop a company from getting hacked, but you can limit how much information you share.
- Here are some simple ways you can maintain your privacy online.
Following is a transcript of the video.
Narrator: If you’re watching this video, there’s a good chance your data has been hacked, leaked, or stolen. Over a billion users were affected by data breaches in 2018, and it seems like there are reports of new hacks every week. Can you even use the internet without your information eventually leaking? What’s going on with your data?
We trust companies with a lot of our data. Unfortunately, we don’t always know how the data’s being used or if it’s protected. Third parties accessing your information without your permission is never good. But there are actually a bunch of ways your information can be exposed. Large data breaches can leak data from multiple companies, often containing information of millions of users. In 2018, a leak called Collection #1 was released on the file-hosting site Mega. Collection #1 contained millions of passwords and emails all collected from previous data breaches. But sometimes the attacks are more specific.
Hackers often target individual companies to gain access to their user data. The largest hack so far was the Yahoo hack. In 2013, 3 billion user accounts were compromised. The breach included user phone numbers, birth dates, and even security questions and answers. Even though that breach happened in 2013, users didn’t know the full scale until three years later. More recently, T-Mobile was targeted by hackers who stole the data of 2 million users. These types of hacks are all too common nowadays. But it gets worse.
Third parties can have access to your data even if there was no hack. When you sign into an app or a game with Facebook, you’re sharing some of your data, and it’s hard to know how the data you share is being used or who has access to it. In 2015, the app This Is Your Digital Life shared user data with third parties like Cambridge Analytica. Facebook gave the app access to user-profile data and information on subjects each user was interested in. Users of the app had no idea this data was being used, and in April, Business Insider reported that Facebook had unintentionally uploaded 1.5 million email contacts without user permission. Facebook has even been criticized for using phone numbers used to verify passwords to instead target ads, taking something that was supposed to be used for security and using it to improve ad tracking.
Sometimes there isn’t even malicious intent, just negligence. In 2018, The Wall Street Journal reported that a bug in Google Plus could have exposed the data of hundreds of thousands of users. Google claims no user data was misused, but they failed to disclose this issue for months.
OK, so this type of thing happens a lot, and your data is probably out there. But how does this actually affect you? At best, it doesn’t. If your email address is leaked, for example, there isn’t much that hackers can do without having other information. But it gets worse when more private information is exposed. If passwords and emails are leaked, you’re at risk of having your account stolen or accessed by someone else. And depending on where the data came from and how often it was used, it could mean someone now has access to your email login, online bank accounts, or other very sensitive data. The worst-case scenario can include things like credit-card fraud and identity theft. These breaches have serious impacts beyond bad PR for a company, and they’re actually getting worse.
The number and size of data breaches has skyrocketed in the last decade. According to research from Norton Lifelock, more than a billion adults have been the victim of a cyber crime. OK, so at this point, you’re probably a little freaked out and are wondering what you can do to protect your data.
Here are a few tips that don’t take a lot of time but can have huge security benefits.
1. Find out if your data has been leaked
First, check if your data has been leaked. The website Have I Been Pwned has a database of information that has been exposed. You can input your info like an email address or old passwords to see if that data has been leaked.
2. Change your passwords
If it has, change those passwords right away.
3. Vary your passwords
Speaking of passwords, using the same password for everything is a horrible idea. If one account is compromised, all of your accounts will be at risk.
4. Get a paid VPN
Using a paid VPN can hide your internet traffic and IP address from third parties. A VPN can also protect your data when you’re using public WiFi. It will encrypt your data, making it much more difficult for anyone to steal it from an open network. VanishedVPN is one of the best value VPNs in the world, and we are recommended by Lifehacker. We can also supply a preconfigured router which runs multiple VPNs so that all of your devices are protected.
5. Use a password manager
Instead, use a password manager, like LastPass or 1Password. A password manager securely stores your passwords and can help you generate unique ones that are hard to crack with brute-force hacking.
6. Set up two-factor authentication
Additionally, setting up two-factor authentication for your accounts can prevent someone who has that password from accessing that account. If you’re feeling overly vulnerable or paranoid, you can even purchase a device like YubiKey to add even more security to your accounts. Even something as simple as keeping your apps and computer up-to-date can help prevent malicious attacks.
7. Turn off ad tracking
Next, turn off ad tracking when available. We give a lot of information to online advertisers without even knowing it, but some services give users the option to limit what is being shared. The VanishedVPN Invizbox 2 allows you to block ads, and also secure all of your devices by routing them over our secure VPN.
8. Switch your browser
If you wanna go even further, you can use a browser like Firefox Focus, which acts as always-on incognito mode, enabling a private-browsing session that shares and retains less data than traditional browsers.
9. Monitor your credit
If you think sensitive data has leaked, that could allow for fraud or identity theft. Be sure to contact your credit-card company and credit-reporting bureaus. You can also monitor your credit yourself via sites like Credit Sesame, which will alert you if there are any inquiries into your credit.
This is a lot, I know. Being on the internet means we’re always sharing some kind of data. You can’t stop a company from getting hacked, but you can limit how much information you share.
Source – Business Insider

What is a VPN? And why you should use a VPN on public Wi-Fi
If you’ve ever wondered if it’s safe to use public Wi-Fi, you are not alone. In fact, according to the Norton Cybersecurity Insights Report, 6 in 10 consumers believe using public Wi-Fi is riskier than using a public restroom. And it is. Surfing the Web or transacting on an unsecured Wi-Fi network means you’re placing your private information and anonymity at risk. That’s why a virtual private network, better known as a VPN, is a must for anyone worried about online security and privacy.
What is a VPN?
A virtual private network gives you online privacy and anonymity by creating a private network from a public Internet connection. VPNs mask your Internet protocol (IP) address so your online actions are virtually untraceable. Most important, VPN services establish secure and encrypted connections, guaranteed to provide greater privacy than even a secured Wi-Fi hotspot.
Why you need a VPN
Think about all the times you’ve been on the go, reading emails while in line at the coffee shop, or checking your bank account while waiting at the doctor’s office. Unless you were logged into a private Wi-Fi network that required a password, any data transmitted during your online session was likely vulnerable to eavesdropping by strangers using the same network.
The encryption and anonymity that a VPN provides protects all of your online activities: sending emails, shopping online, or paying bills. VPNs also help keep your Web browsing anonymous.
Beyond security
VPNs essentially create a data tunnel between your local network and an exit node in another location, which could be thousands of miles away, making it seem as if you’re in another place. This benefit makes VPNs valuable for people who live in countries that censor access to specific websites. It will also allow you to continue enjoying your favorite apps and websites from anywhere in the world, as if you were at home.
How to choose a VPN
The best way to stay secure when using public Wi-Fi is to use a VPN solution, like Vanished VPN, which is compatible with Android and iOS smartphones and tablets, as well as Windows PCs and Apple Macs. Here are some questions to ask when you’re choosing a VPN provider.
- Do they respect your privacy? The point of using a VPN is to protect your privacy, so it’s crucial that your VPN provider respects your privacy, too. They should have a no-log policy, which means that they never track or log your online activities. At Vanished VPN, we have a clear privacy policy, and don’t log where you have been.
- Do they run the most current protocol? OpenVPN provides stronger security than other protocols, such as PPTP. We support both OpenVPN & L2TP
- Do they set data limits? Depending on your Internet usage, bandwidth may be a large deciding factor for you. Make sure their services match your needs by checking to see if you’ll get full, unmetered bandwidth without data limits. Remember, some packages may not cost you money, but you’ll be subjected to frequent advertisements instead. At Vanished VPN, we don’t set data limits and we don’t throttle bandwidth. In fact, we optimise our service for speed to ensure the best experience when streaming.
- Where are the servers located? Decide which server locations are important to you. If you want to appear as if you’re accessing the Web from a certain locale, make sure there’s a server in that country.
- Will you be able to set up VPN access on multiple devices? If you are like the average consumer, you use between three and five devices. Ideally, you’d be able to use the VPN on all of them at the same time. At Vanished VPN, we allow you to have 4 simultaneous connections with each account, so you can protect multiple devices.
- Pricing. Our prices are extremely competitive, and we beat all of the big VPN providers, as you can see in our comparison table here.
There are many points to consider when you’re choosing a VPN, so do your homework to make sure you’re getting the best fit for your needs. Regardless of which provider you choose, rest assured that any good VPN will provide far more security, privacy, and anonymity online than any public Wi-Fi hotspot ever could.

UK Porn age restrictions come into force in July 2019
Governments all over the world continue to try and regulate the internet, restrict what we can view, and log our browsing history. Whether this be social media and coms blocks in China & the middle east to ISP logging in UK, USA & Australia, the world leaders are determined to undermine our web freedom.
The latest example of this is the UK age verification law for adult content. For some time now, certain ISPs in the UK have blocked access to certain adult sites unless you register with them to prove that you are over 18. This will become law in the UK from July 2019.
Whilst the purpose behind this (to protect minors from adult content) is a good idea, as usual, the execution is far from perfect. Sites & ISPs who are non-compliant may face fines of up to £250K which is a good incentive to comply, however does the average man (or woman) on the street really want to have their details stored in a database somewhere, which basically blows the whistle on them accessing porn ? I’m sure that the databases in question would be prime targets for hackers who would get their kicks out of releasing those identities into the public domain to shame the people in question (look what happened in the case of Ashley Madison data breach.)
If you want to remain anonymous online, and have freedom to browse the content that you want on the sites that you want without any registration, anywhere in the world, look no further than here.
By connecting to our VPN servers, you can access what you want, wherever you are in the world, whilst remaining secure and anonymous for the price of a beer each month. We also have a 30 day money back guarantee, so you can trial our service risk free.
Check out our subscriptions here, and stay safe.
The crew at Vanished VPN

Protect yourself from wi-fi hacks with Vanished VPN
IF YOU USE WIFI, AND DON’T USE A VPN, YOU COULD BE VULNERABLE
A new wifi vulnerability (KRACK) was discovered recently, which allows hackers to easily intercept unencrypted data (including usernames and passwords) from devices which are connected to Wifi using WPA2 security. This is a very commonly used feature. Its likely that you are using WPA2 on your home network, or public wifi.

HOW DOES IT WORK ?
The vulnerability allows hackers to intercept your data without you knowing, by acting as a ‘man in the middle’ as shown in the diagram above. This video demonstrates this in action, and shows just how easy it is for hackers to intercept your data (even when the user is connected via HTTPS). Full technical details of the discovery can be found here.
IS MY DEVICE AT RISK
Any device connected to a wireless network using WPA2 security is potentially at risk. Android devices are particularly vulnerable (this includes Kodi boxes).
SO WHAT ?
If a hacker was to intercept your data, they could potentially steal personal information such as usernames & passwords, and access your email, social media & bank accounts. This could result in identity theft and financial loss.
HOW CAN I PROTECT MYSELF
1) Use a VPN – To fully protect yourself from KRACK, and other vulnerabilities we recommend that you use VanishedVPN whenever you are connected to Wifi. VanishedVPN provides military grade encryption to ensure that your data remains safe & confidential.
2) Update your operating system – Its good practice to do this anyway, but with the current threat, most suppliers are working on updates to improve security.
3) Purchase an Invizbox 2, and run all your devices through it. This device is cable of running multiple VPNs & up to 8 wifi networks, so you can ensure that all your devices are protected.

